← laying out risk analysis Risk assessment template management plan fire project manufacturing templates example excel questionnaire health construction property sample examples table sheet schools qualitative vs quantitative risk analysis Qualitative vs quantitative risk analysis what s the →
If you are searching about How to Perform a Cybersecurity Risk Assessment: A Step-by-Step Guide you've visit to the right web. We have 35 Pics about How to Perform a Cybersecurity Risk Assessment: A Step-by-Step Guide like How to Perform a Cybersecurity Risk Assessment: A Step-by-Step Guide, Why You Need a Cyber Security Risk Assessment | PamTen and also Cybersecurity Risk Assessment – A Better Way - Virtual CISO. Read more:
How To Perform A Cybersecurity Risk Assessment: A Step-by-Step Guide
 www.alpinesecurity.com
www.alpinesecurity.com
risk assessment cybersecurity
Cyber Security Risk Assessment Matrix PPT Slide
 www.slideteam.net
www.slideteam.net
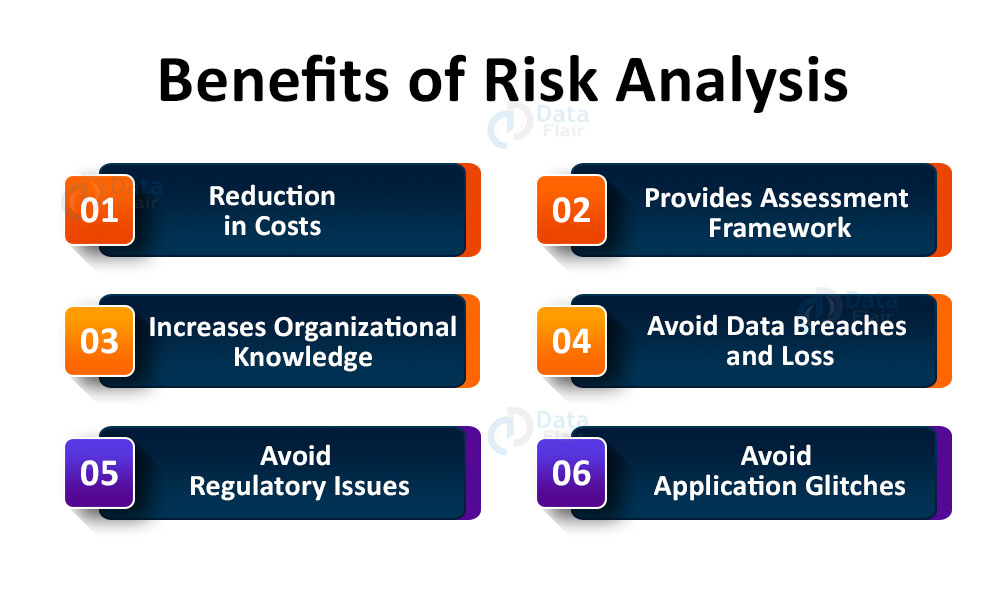
Cyber Security Risk Analysis And Assessment - DataFlair
 realha.us.to
realha.us.to
Risk Assessment Flowchart For Cyber Security Management
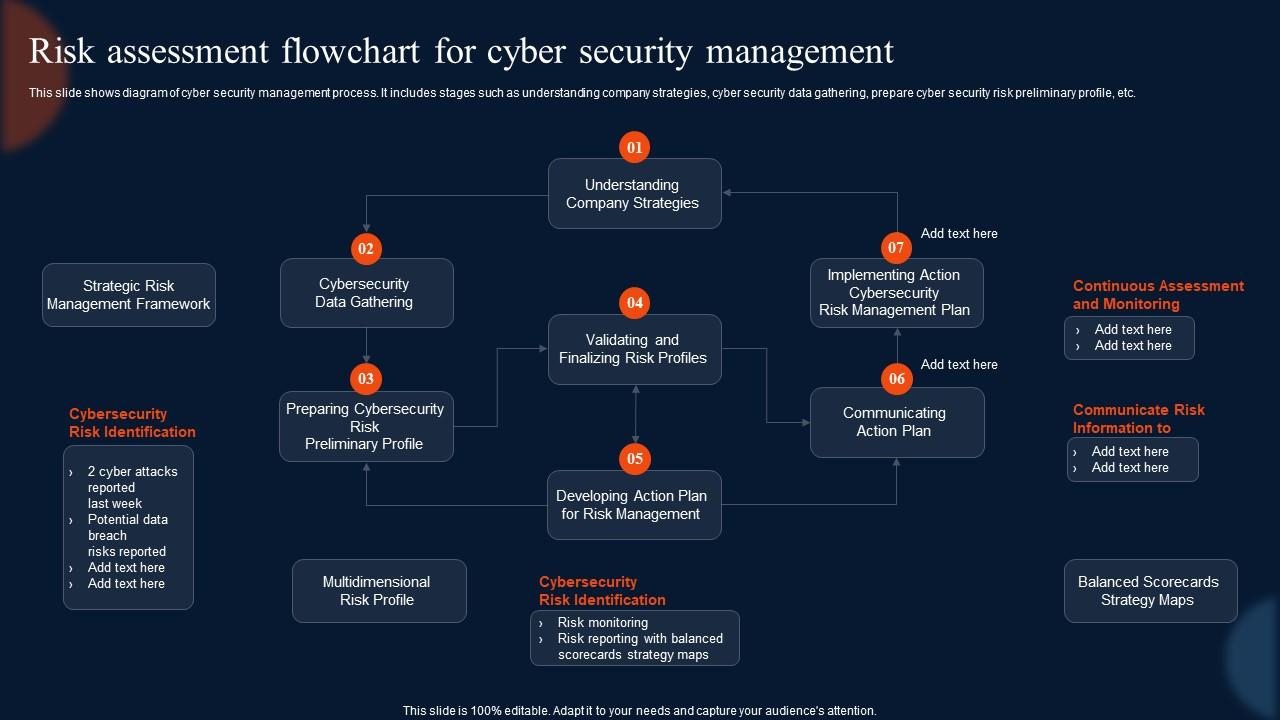 www.slideteam.net
www.slideteam.net
Cybersecurity Risk Assessment: Create Your First One Now | Liquid Web
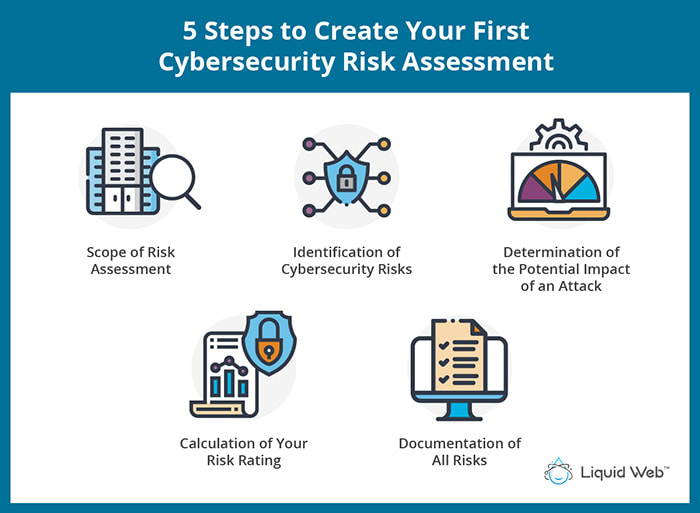 lwgatsby.s3-website.us-east-2.amazonaws.com
lwgatsby.s3-website.us-east-2.amazonaws.com
Quantitative Metrics And Risk Assessment: The Three Tenets Model Of
 www.pinterest.com
www.pinterest.com
assessment threat risk cyber security model cybersecurity tenets quantitative metrics information integrity confidentiality availability three vulnerabilities management models life vulnerability
How To Conduct A Cybersecurity Risk Assessment | ConnectWise
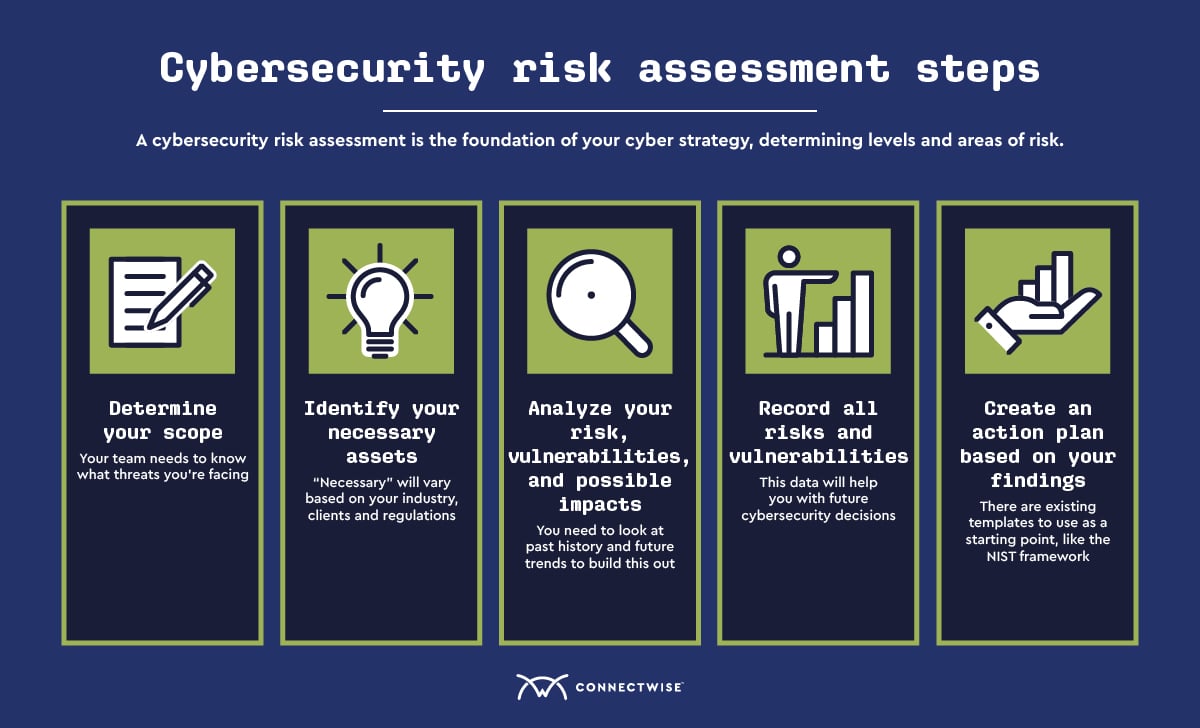 www.connectwise.com
www.connectwise.com
Cyber Security Risk Analysis And Assessment - DataFlair
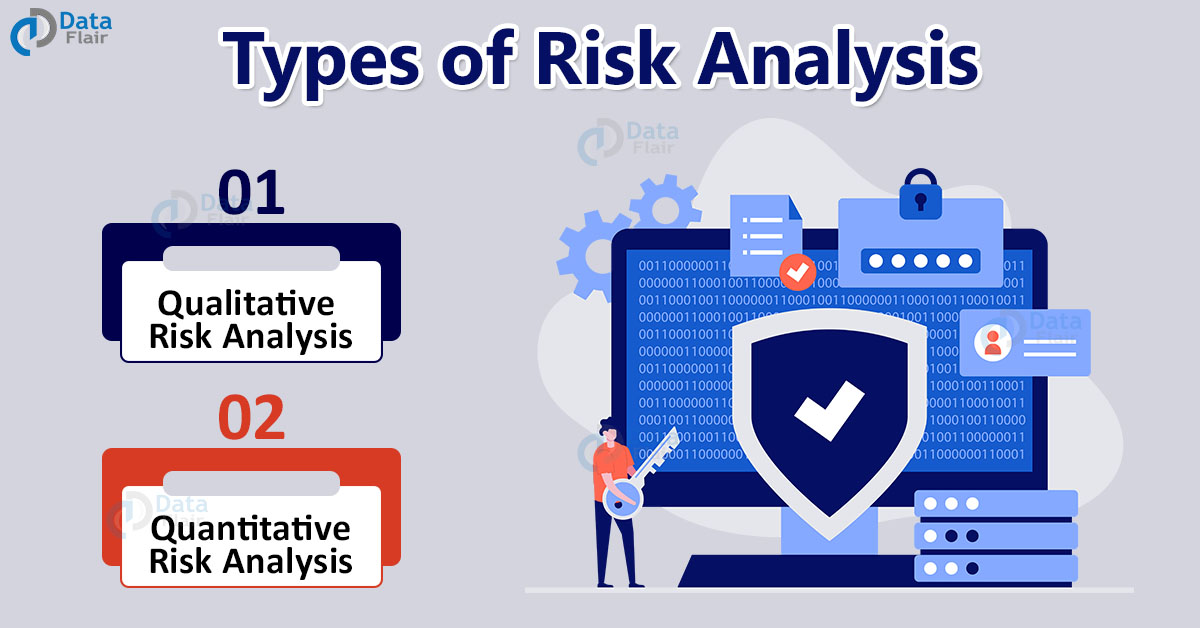 data-flair.training
data-flair.training
Cybersecurity Risk Assessment – A Better Way - Virtual CISO
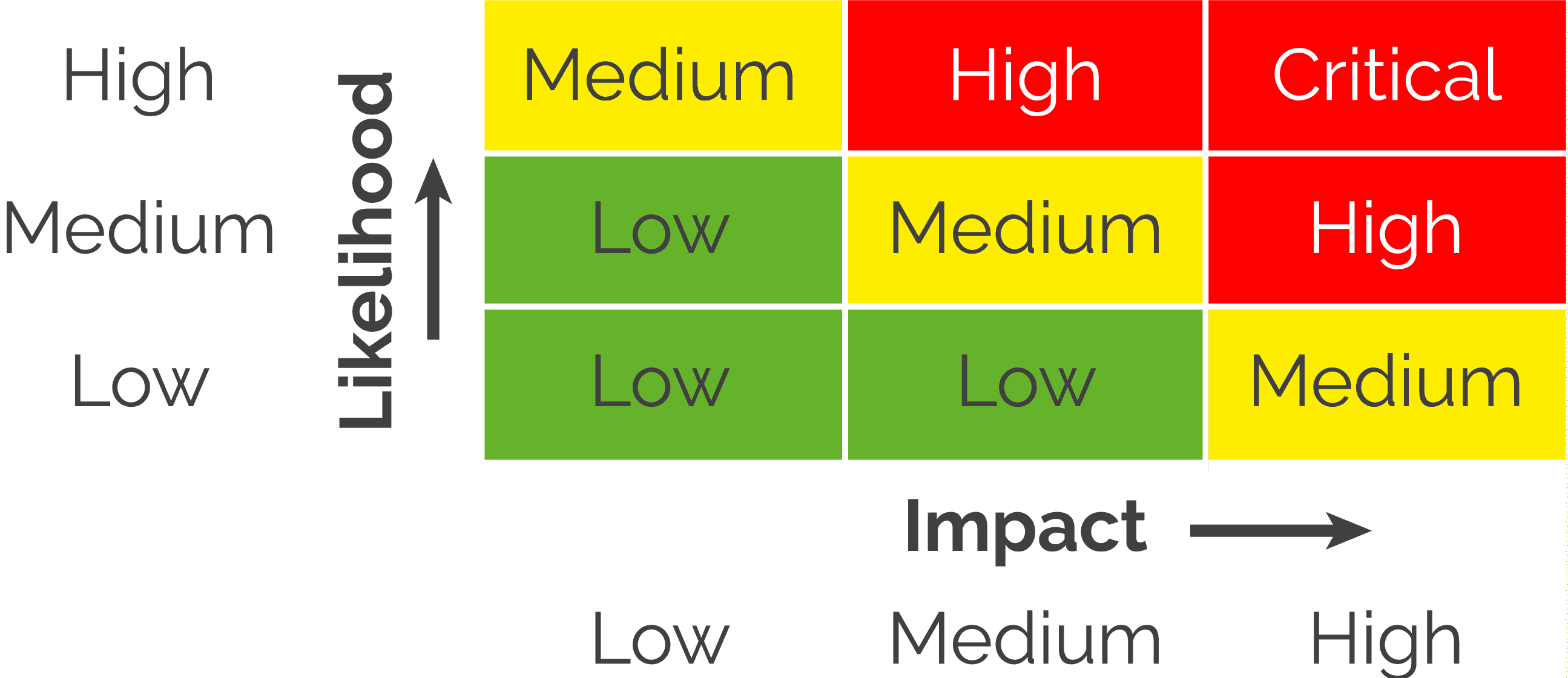 fractionalciso.com
fractionalciso.com
risk cybersecurity matrix assessment impact likelihood vs traditional better way
What Is A Cyber Security Risk Assessment? - PlexTrac
 plextrac.com
plextrac.com
Information Security Risk Assessment Template - Uses NIST 800-171
 www.complianceforge.com
www.complianceforge.com
risk assessment template security cybersecurity control information matrix cyber example maturity templates nist examples management raw compensating plan may document
Cybersecurity Risk Analysis Chart With Severity And Probability
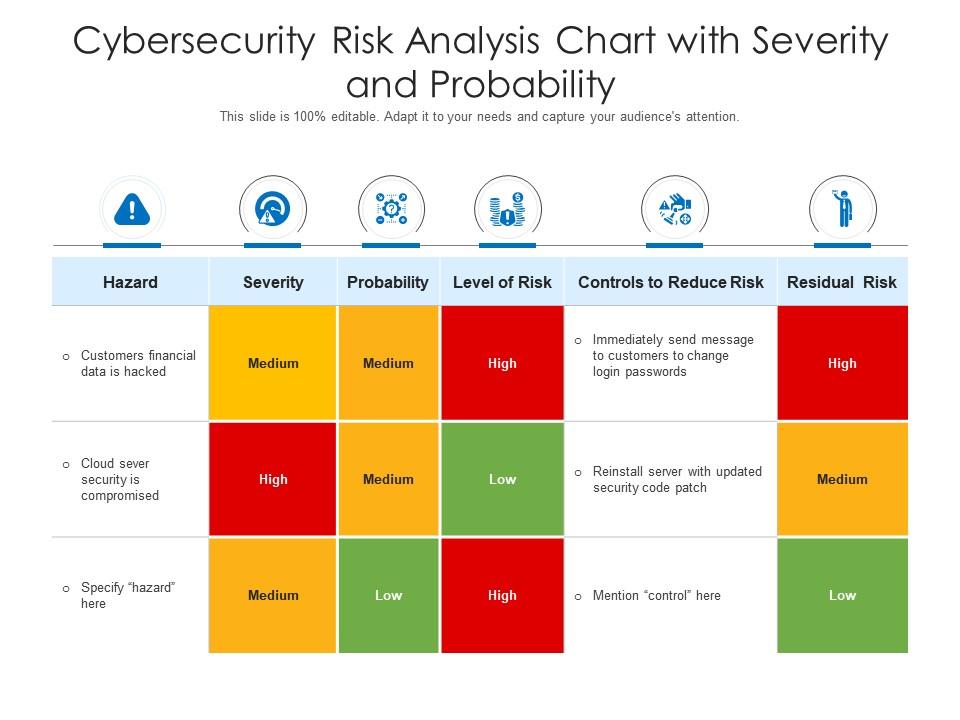 www.slideteam.net
www.slideteam.net
Cyber Security Threat Assessment: How To Manage Risk - WBM Technologies
 www.wbm.ca
www.wbm.ca
security risk threat threats assessment manage wbm identified technologies
Cybersecurity Risk Assessment | Template For Creating Cybersecurity
risk assessment security template cybersecurity cyber matrix nist score information plan analysis controls microsoft word cover hamiltonplastering article
Why You Need A Cyber Security Risk Assessment | PamTen
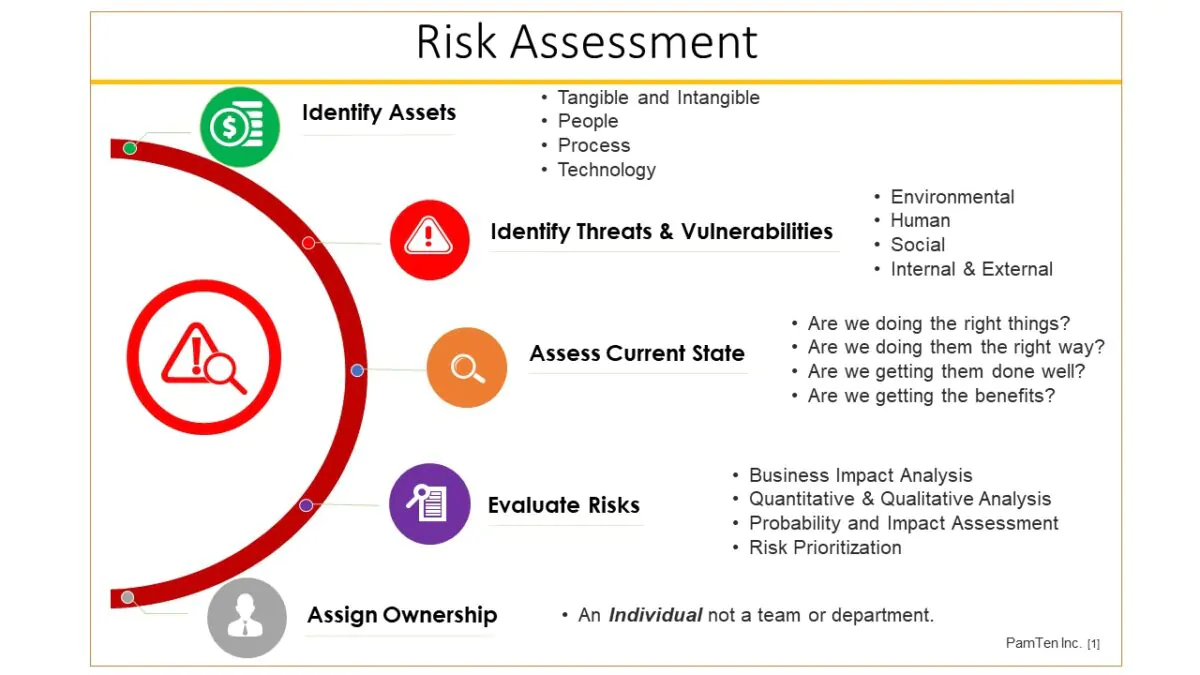 www.pamten.com
www.pamten.com
cyber information
A Risk Manager's Approach To Cyber Security - Compass Cyber Security
 www.compasscyber.com
www.compasscyber.com
cyber risk security risks management treatment methods organization manager which would program like should
Free Cybersecurity Risk Assessment Templates | Smartsheet
 www.smartsheet.com
www.smartsheet.com
Five Steps For Cyber Security Risk Analysis
 www.slideteam.net
www.slideteam.net
Cyber Security Risk Assessment Basics | UND Online
 onlinedegrees.und.edu
onlinedegrees.und.edu
security cyber risk assessment basics und online designated steps done should order
FREE 12+ Sample Security Risk Assessment Templates In PDF | MS Word | Excel
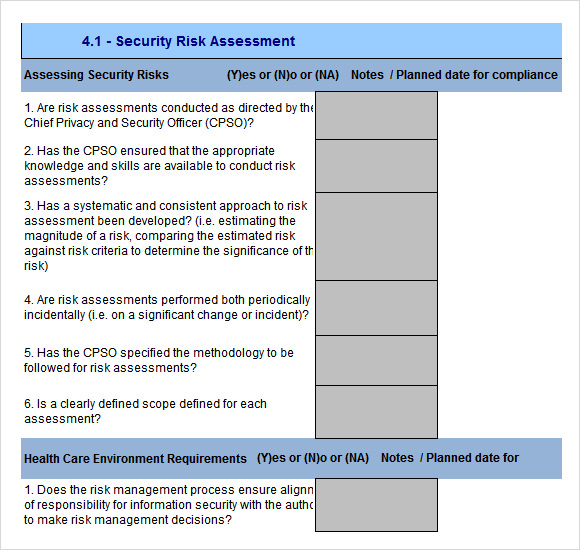 www.sampletemplates.com
www.sampletemplates.com
risk assessment security template plan cyber physical excel sample pdf policy templates analysis word information example checklist management report document
Cyber Security Assessments
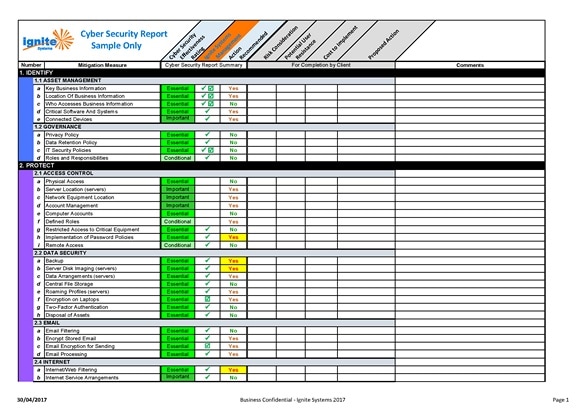 www.ignite.com.au
www.ignite.com.au
security cyber assessment risk report sample matrix capabilities
The Risk-based Approach To Cybersecurity - Moving Away From The Check
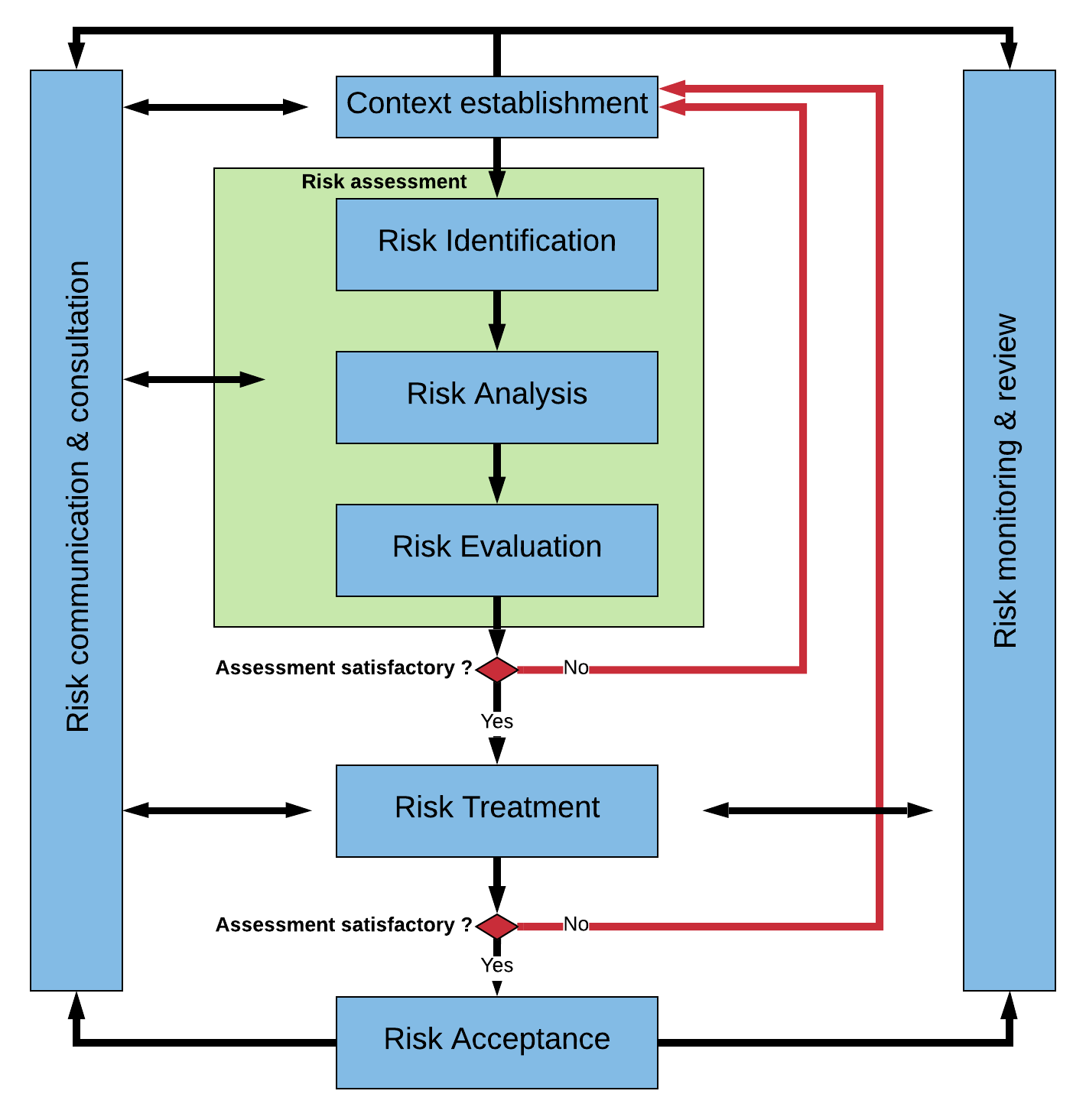 digisoter.com
digisoter.com
Free Cybersecurity Risk Assessment Templates | Smartsheet
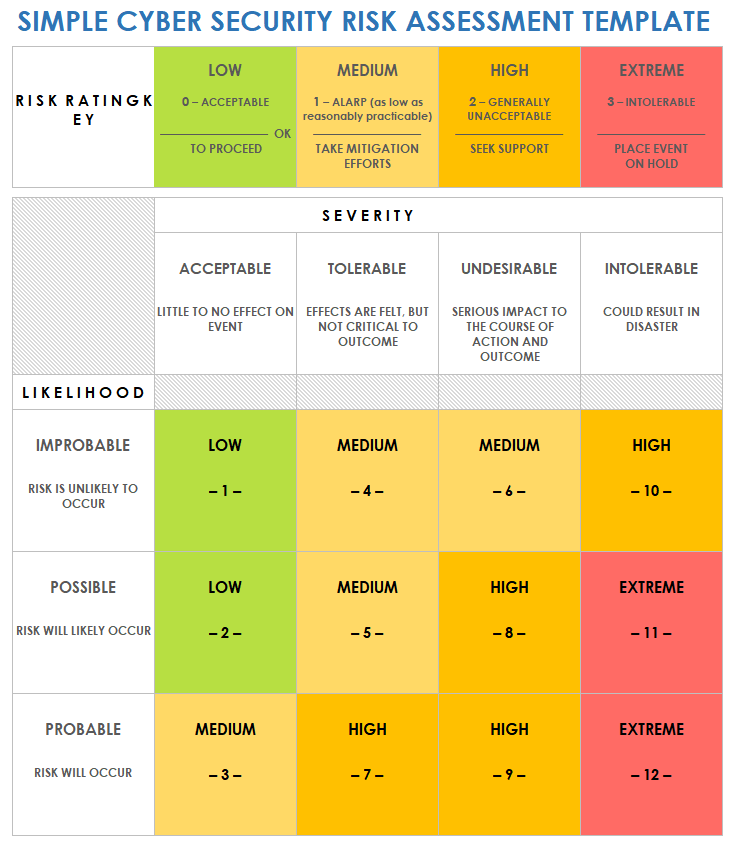 www.smartsheet.com
www.smartsheet.com
Cyber Risk Assessment: What Is It And How Do You Perform One?
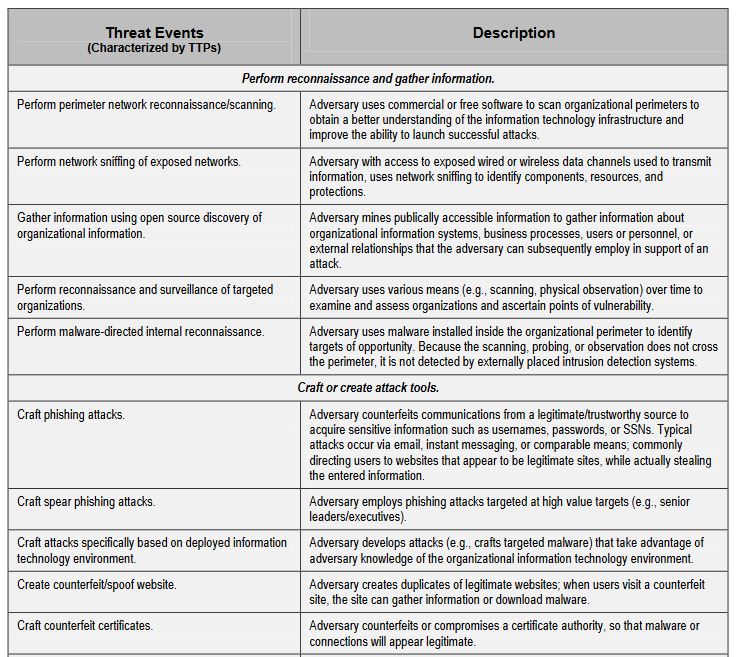 www.thesslstore.com
www.thesslstore.com
risk assessment cyber security template report example threat table impact checklist vulnerabilities survey attack form site identify likelihood would audit
Cybersecurity Risk Assessment (CRAT) – Security Waypoint
 securitywaypoint.com
securitywaypoint.com
cybersecurity crat
Cybersecurity Risk Assessments - Free Cyber Score | PCGiT
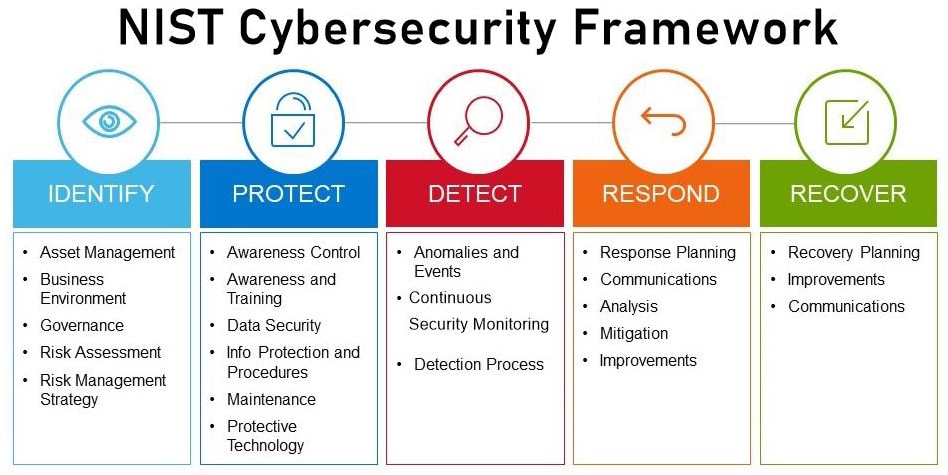 www.pcgit.com
www.pcgit.com
risk security assessment cyber cybersecurity framework detect
Top 6 Cybersecurity Risk Assessment Templates And Tips
Maa Cyber Security Group: Why Is Cyber Security Risk Assessment So
 ethicalhackersindia.blogspot.com
ethicalhackersindia.blogspot.com
Cyber Security Risk Management Plans
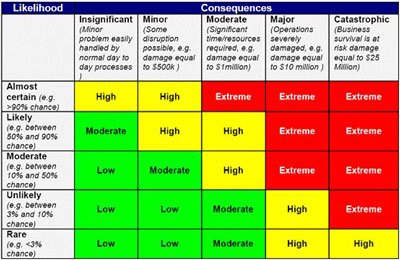 www.securityri.com
www.securityri.com
risk assessment matrix cyber security template management analysis safety cybersecurity project threat rating register health business crisis plan bcp mapping
How To Perform A Cybersecurity Risk Assessment In 5 Steps | TechTarget
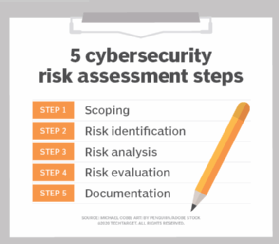 www.techtarget.com
www.techtarget.com
Risk Management Process
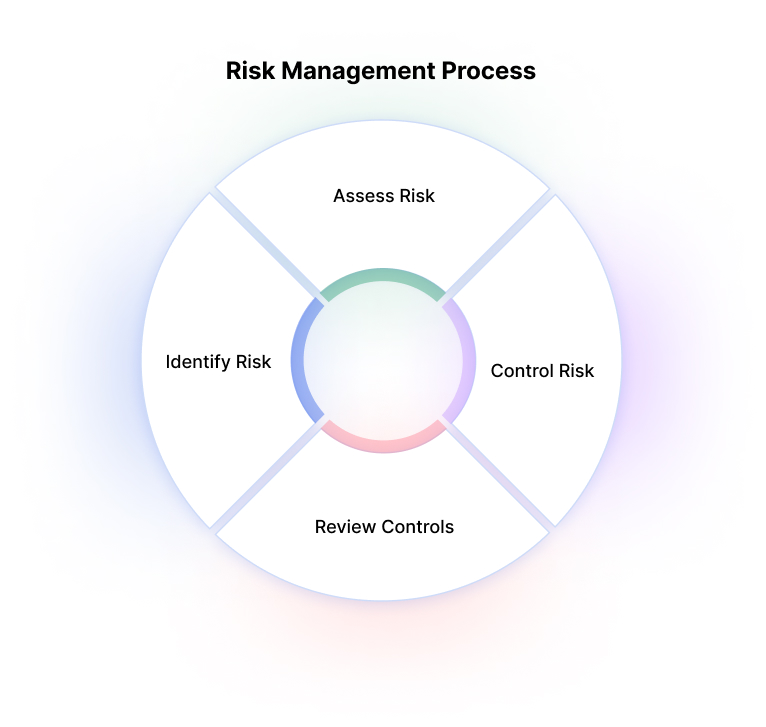 www.imperva.com
www.imperva.com
How To Create An Effective Cybersecurity Risk Management Plan - TitanFile
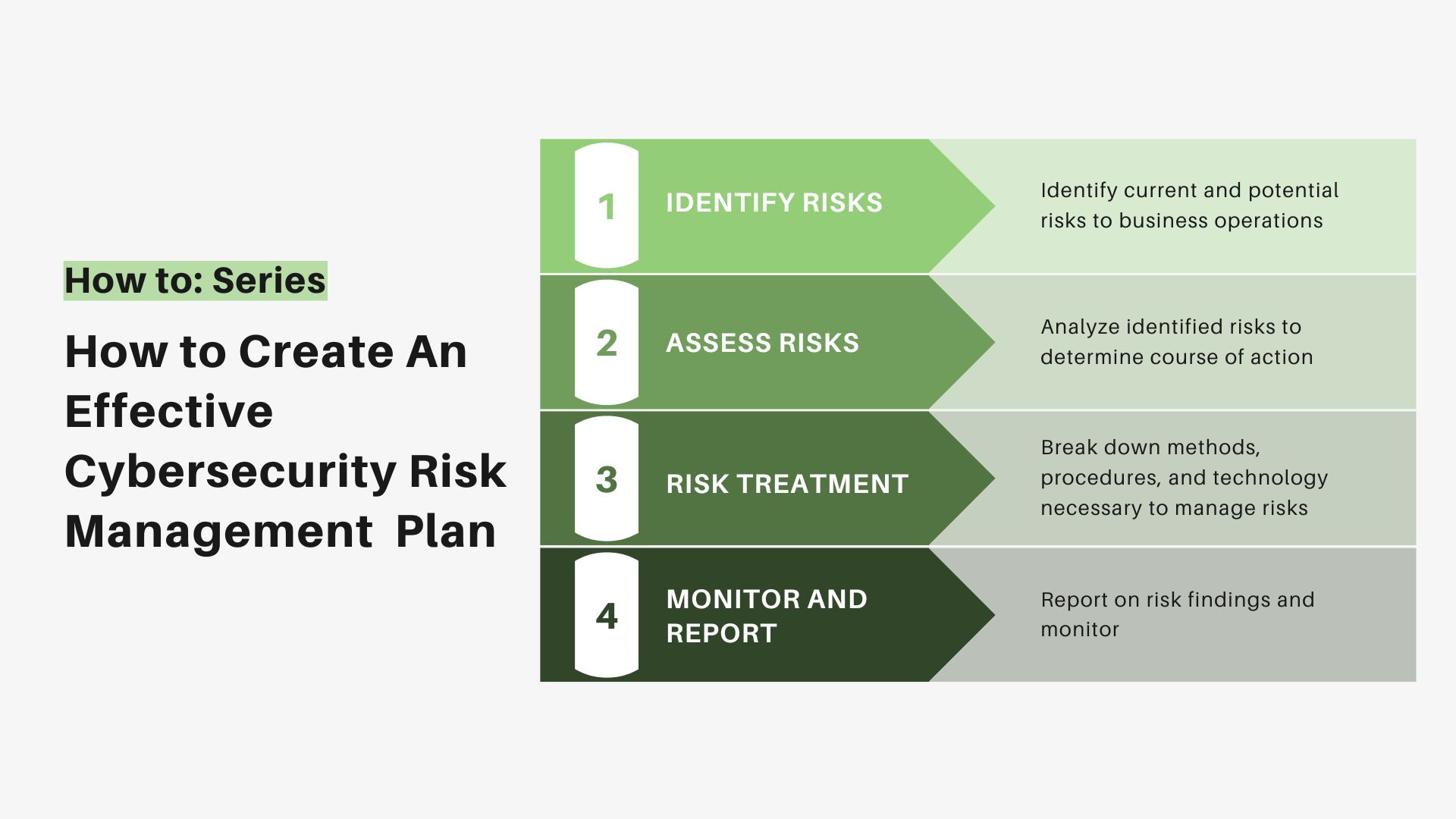 www.titanfile.com
www.titanfile.com
Dynamic Cybersecurity Risk Assessment | Tarlogic
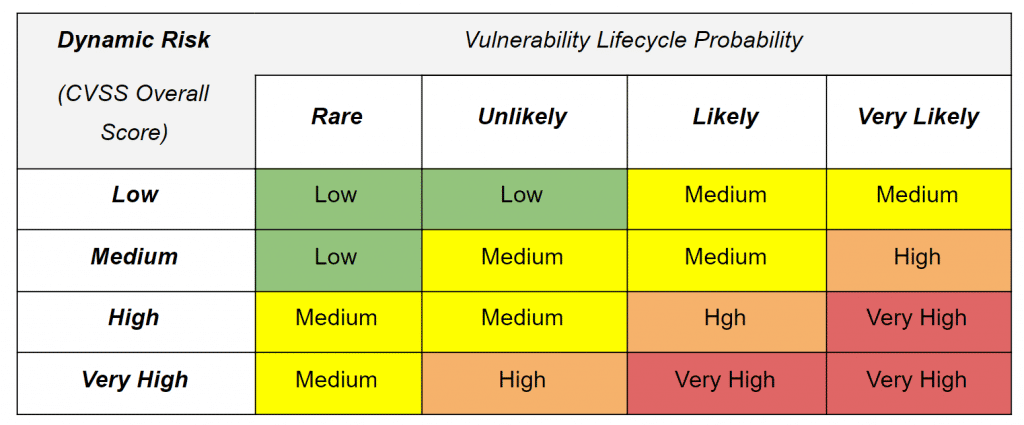 www.tarlogic.com
www.tarlogic.com
How To Conduct A Cybersecurity Assessment
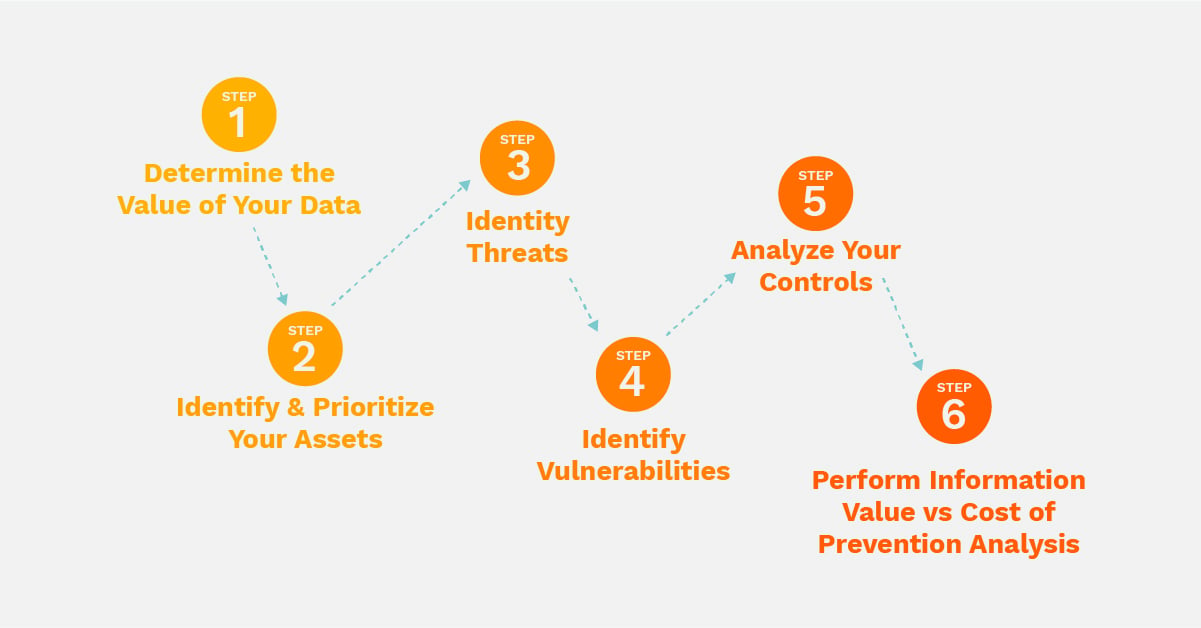 www.office1.com
www.office1.com
cybersecurity assessment risk conduct steps data determine value step conducting
Cybersecurity Risk Assessment Chart For Organization | Presentation
 www.slideteam.net
www.slideteam.net
cybersecurity chart
Cybersecurity risk assessments. How to conduct a cybersecurity assessment. Risk assessment cybersecurity