← warehouse risk assessment dock leveler Sample warehouse risk assessment completed warehouse risk assessment Risk assessment example →
If you are searching about Cybersecurity Risk Management | Cybernetic Global Intelligence you've came to the right web. We have 35 Pictures about Cybersecurity Risk Management | Cybernetic Global Intelligence like Information Security Risk Management | ISMS.online, Information security risk management process | Download Scientific Diagram and also Information Security Dashboard Effective Information Security Risk. Here it is:
Cybersecurity Risk Management | Cybernetic Global Intelligence
 www.cyberneticgi.com
www.cyberneticgi.com
risk management security audit
Information Security Risk Management For ISO 27001/ISO 27002, Third
 www.scribd.com
www.scribd.com
calder alan 3rd itgovernance watkins
Information Security Risk Management | ISMS.online
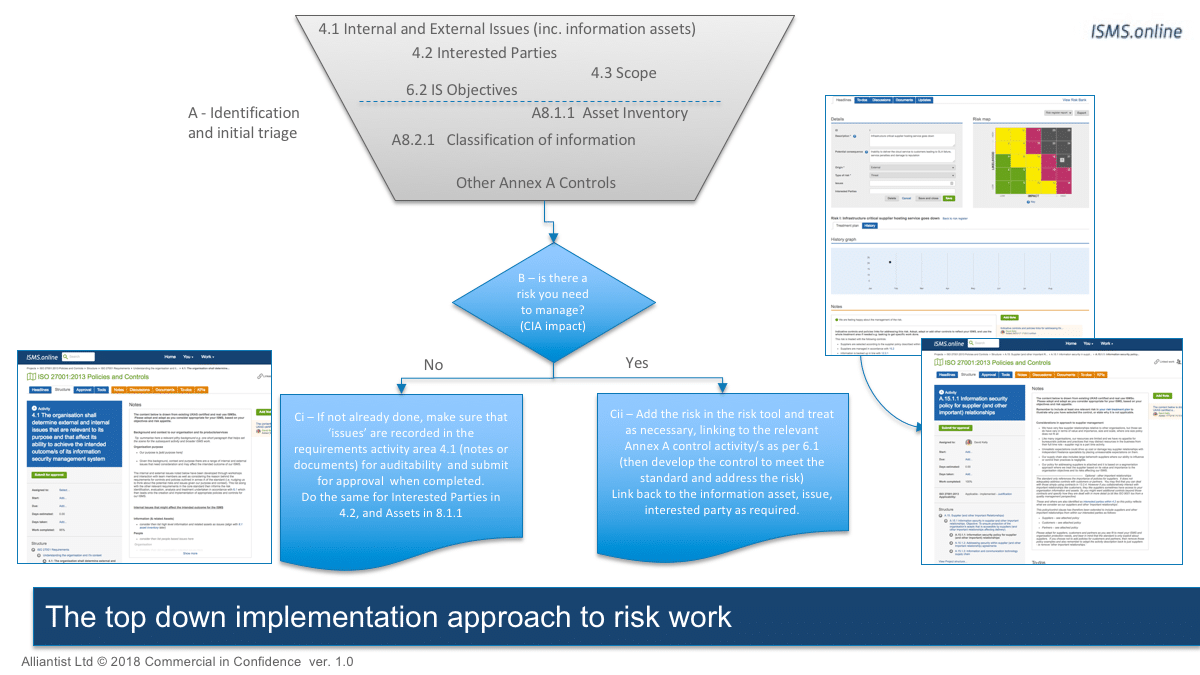 www.isms.online
www.isms.online
risk security management isms information iso process online explained
A Guide To Information Security Risk Management
 linfordco.com
linfordco.com
risk auditor cisa
How To Build An Effective Information Security Risk Management Program
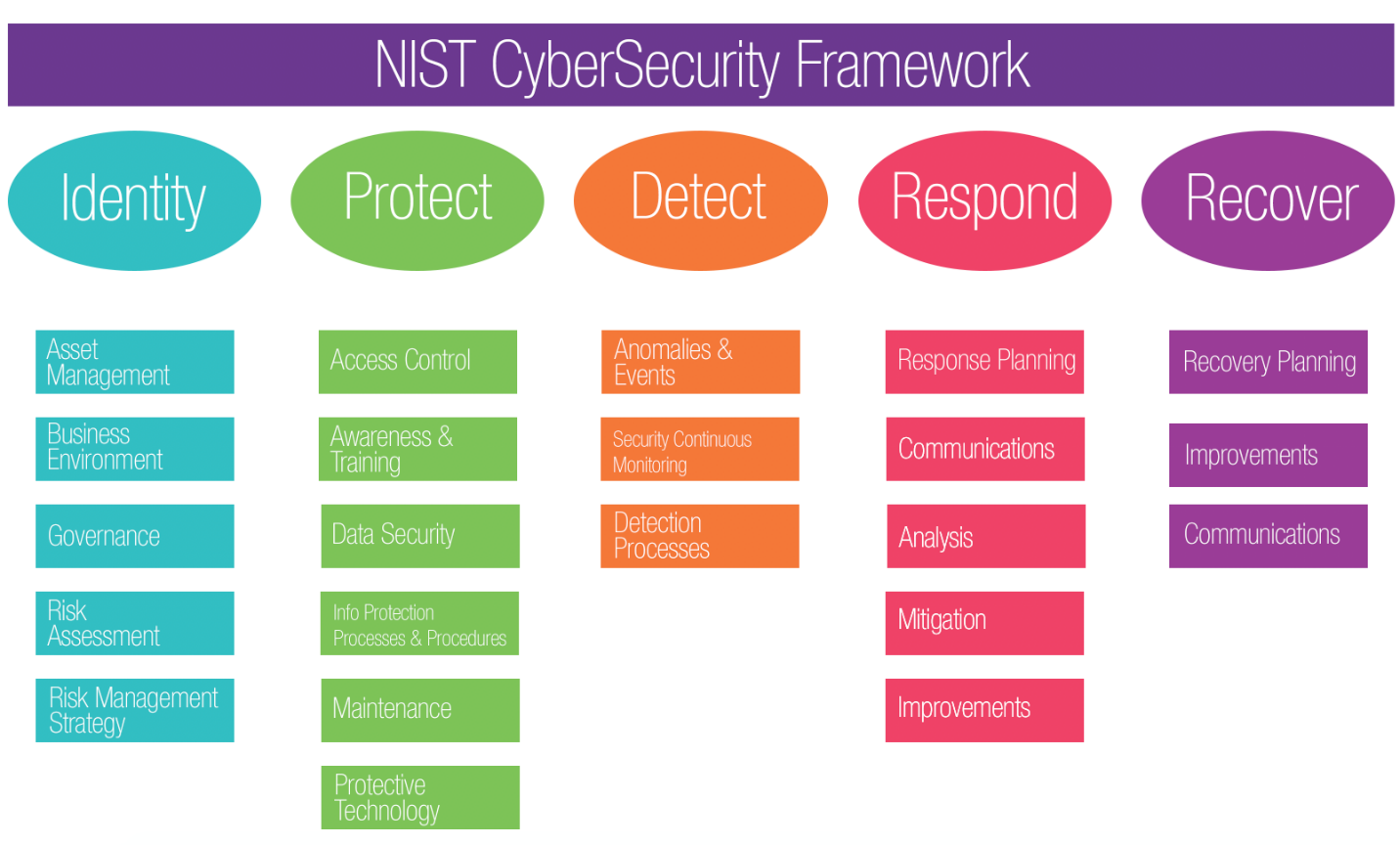 blog.netwrix.com
blog.netwrix.com
cybersecurity nist risikomanagement incidents effective frameworks planning
ISO/IEC 27005 Information Security Risk Management: Foundation
 iquasarcyber.com
iquasarcyber.com
ISO 27005 – Information Security Risk Management | SMATICA LLC
 www.smatica.com
www.smatica.com
Information Security Risk Management Process | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
Risk Management In Information Security - Seguro - Cyber Security
 seguro.ltd
seguro.ltd
Artificial Intelligence Risk Management Model For Information Security
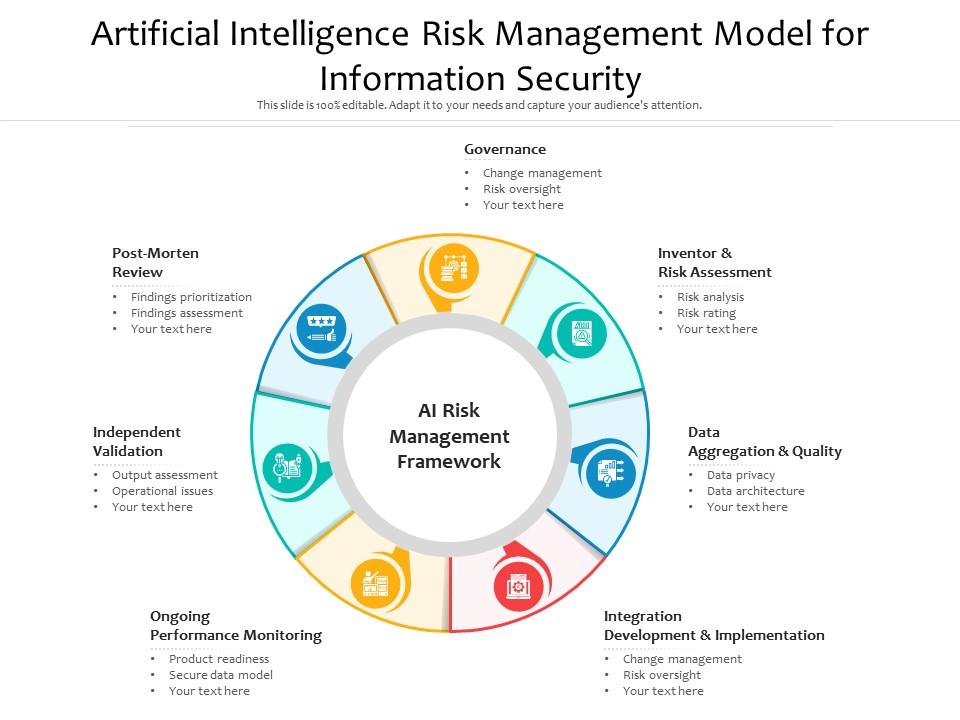 www.slideteam.net
www.slideteam.net
Risk Management Dashboard For Information Risk Assessment And
 www.slideteam.net
www.slideteam.net
Information System Security And Risk Administration Plan Roles And
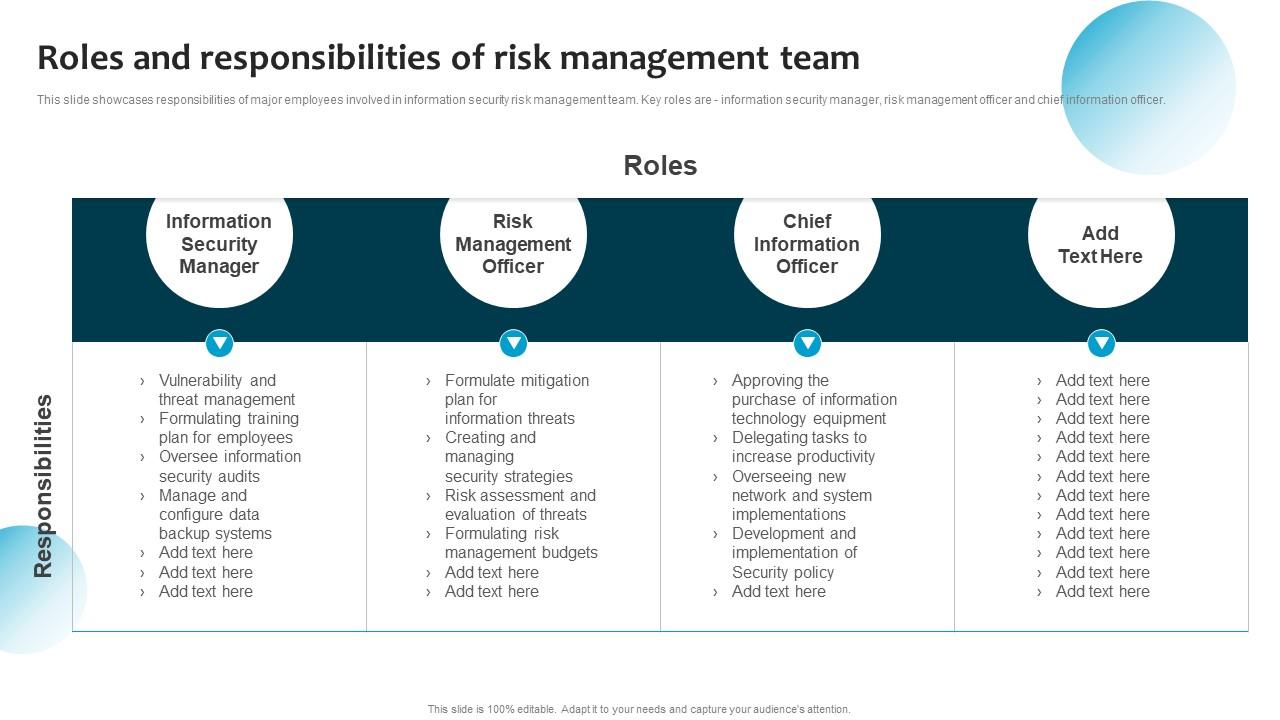 www.slideteam.net
www.slideteam.net
Risk Management Framework - Everything You Should Know
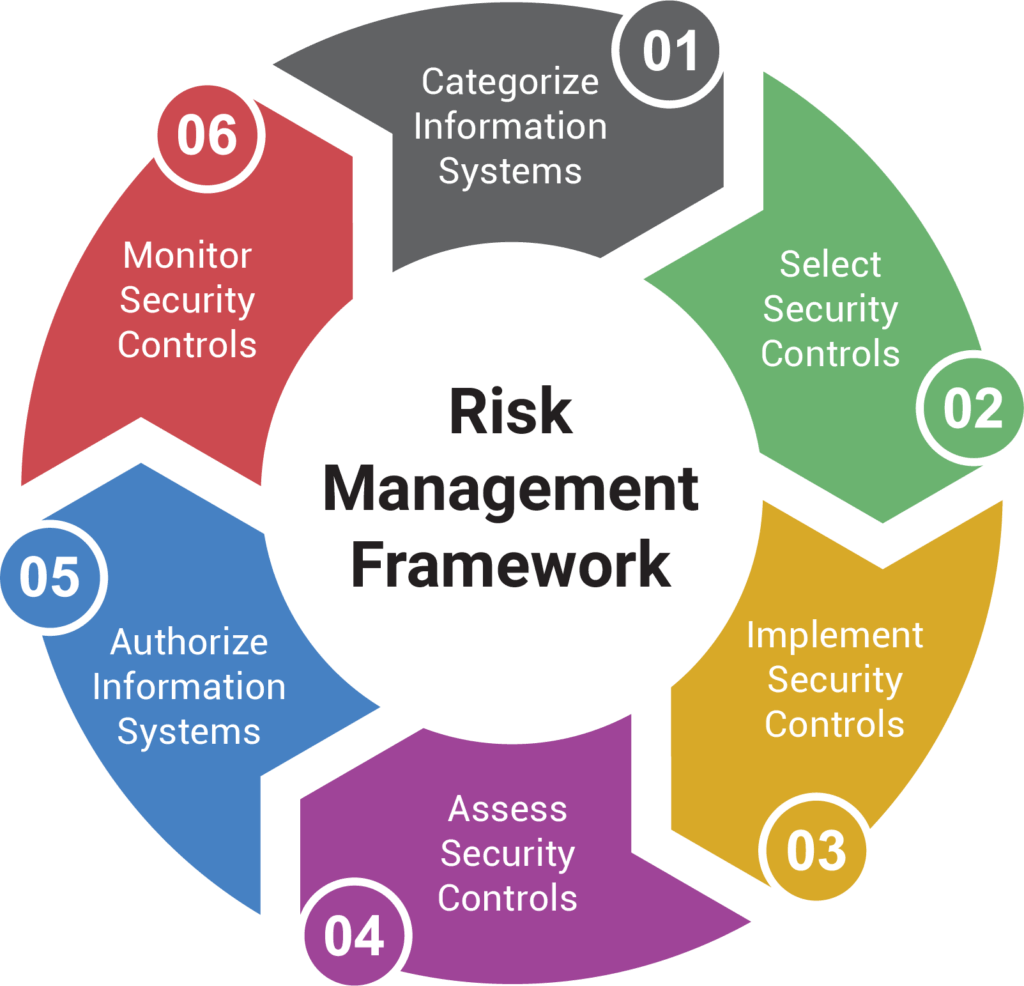 www.mytechmag.com
www.mytechmag.com
Information Security Dashboard Effective Information Security Risk
 www.slideteam.net
www.slideteam.net
How To Perform A Cybersecurity Risk Assessment: A Step-by-Step Guide
 www.alpinesecurity.com
www.alpinesecurity.com
risk assessment cybersecurity
Cyber Security: Security Risk Management | Simplilearn.com
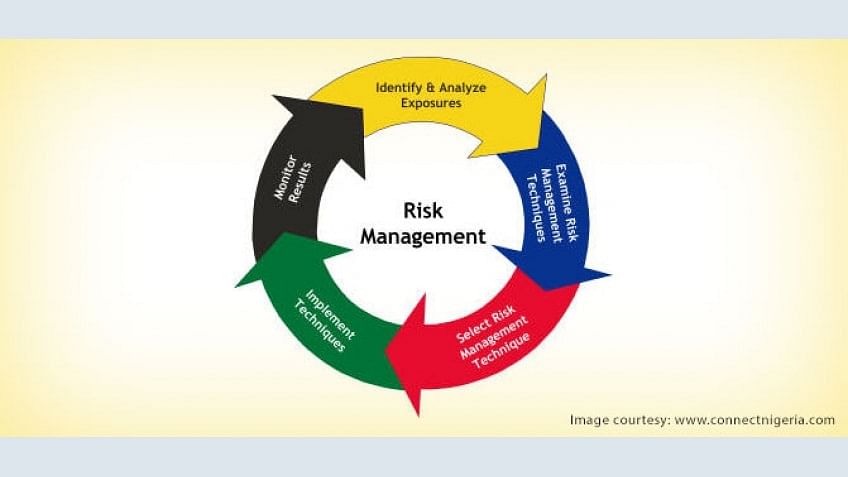 www.simplilearn.com
www.simplilearn.com
cyber simplilearn
QPrime's World: Information Security = Organizational Risk
 qprimesworld.blogspot.com
qprimesworld.blogspot.com
risk management security organizational information world
An 8-Step Risk Assessment For Your Facility's Security - Facilities
 facilitiesmanagementadvisor.blr.com
facilitiesmanagementadvisor.blr.com
importance facility procedure isaca consists
Information Security Risk Assessment And Management Tools
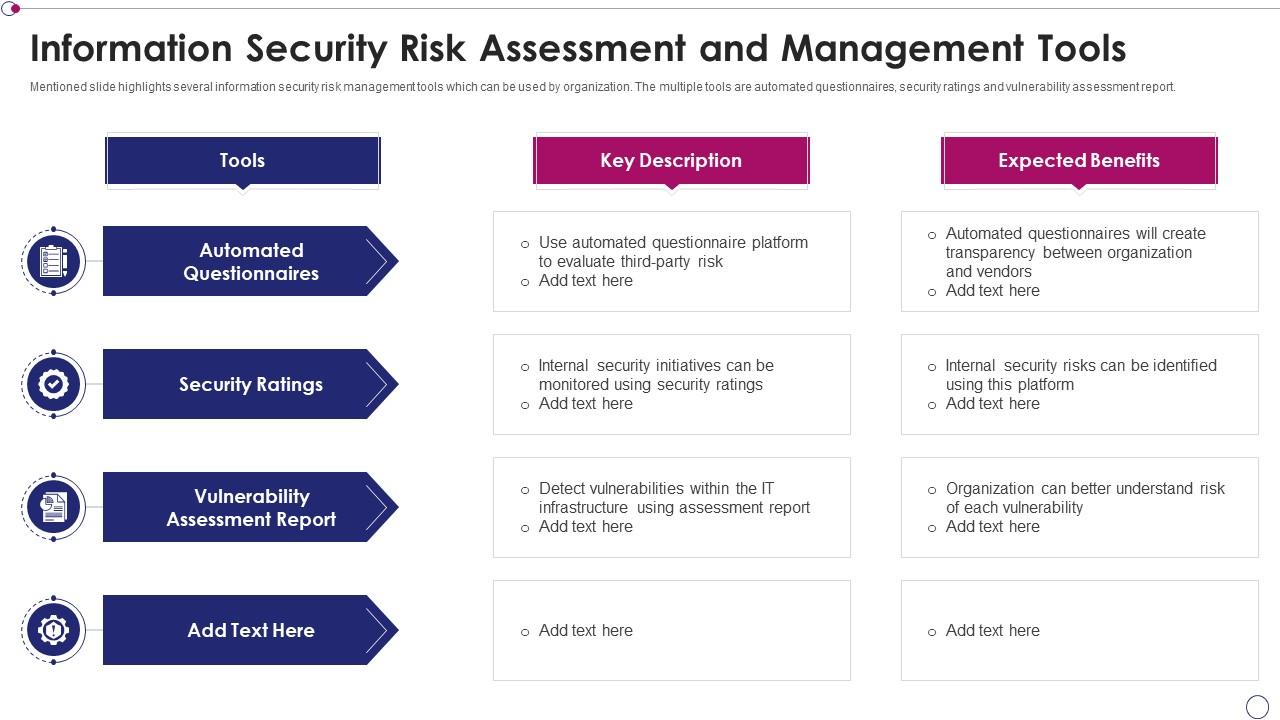 www.slideteam.net
www.slideteam.net
Five Risk Control Strategies | Security Risk Solutions Singapore
 security-risksolutions.com
security-risksolutions.com
control
Information Security Risk Management | ISMS.online
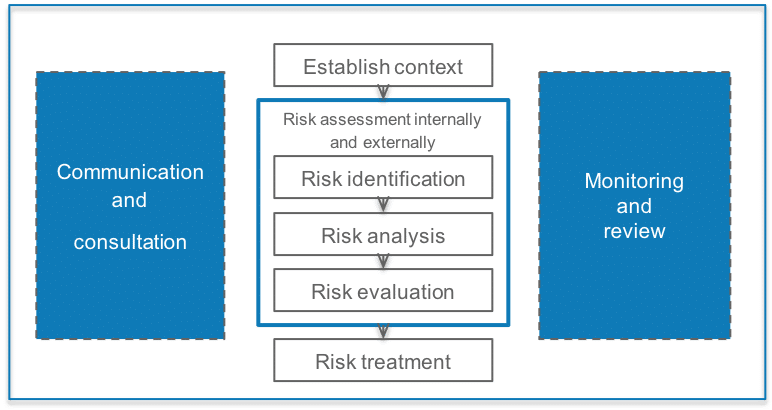 www.isms.online
www.isms.online
risk management security information process iso isms diagram methodology online steps obtain gdpr certification whilst complying mind craft ll our
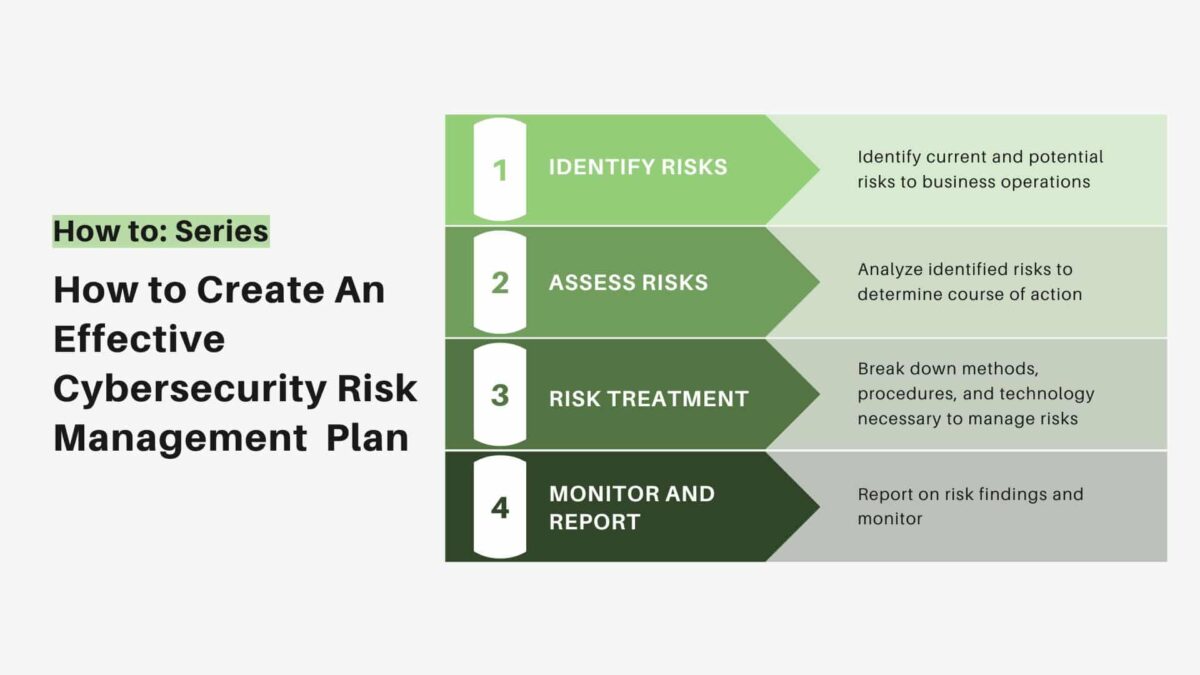
How To Create An Effective Cybersecurity Risk Management Plan - TitanFile
 www.titanfile.com
www.titanfile.com
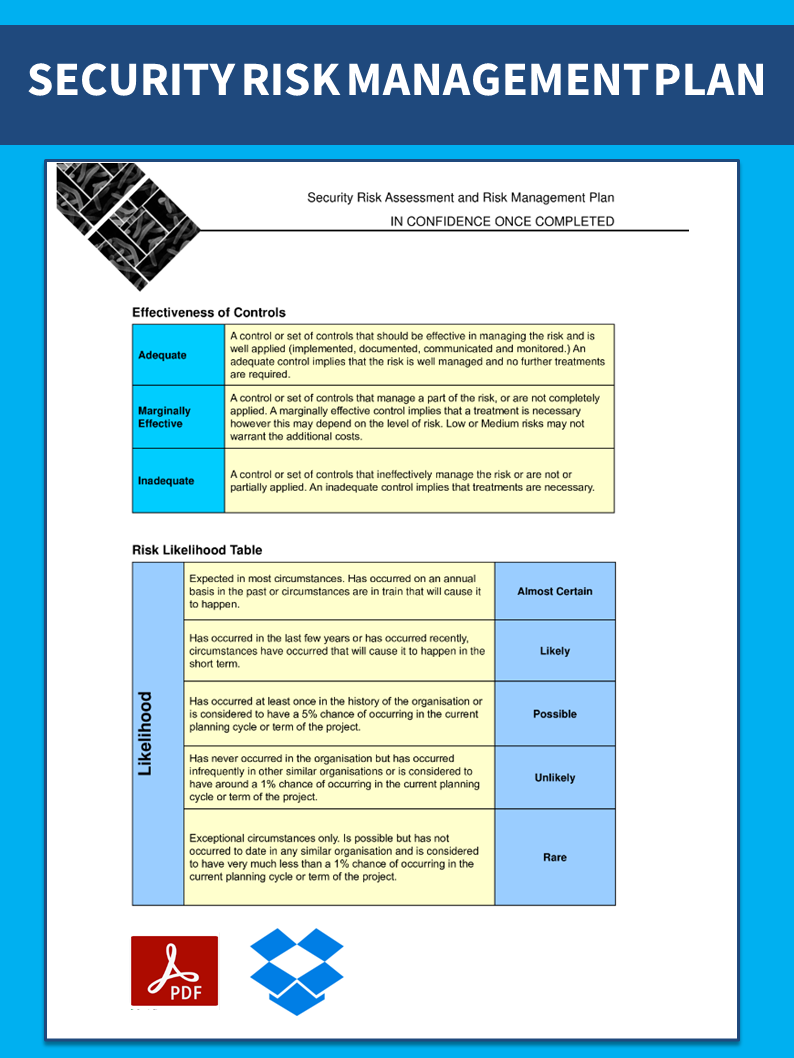
Security Risk Management Plan | Templates At Allbusinesstemplates.com
 www.allbusinesstemplates.com
www.allbusinesstemplates.com
allbusinesstemplates
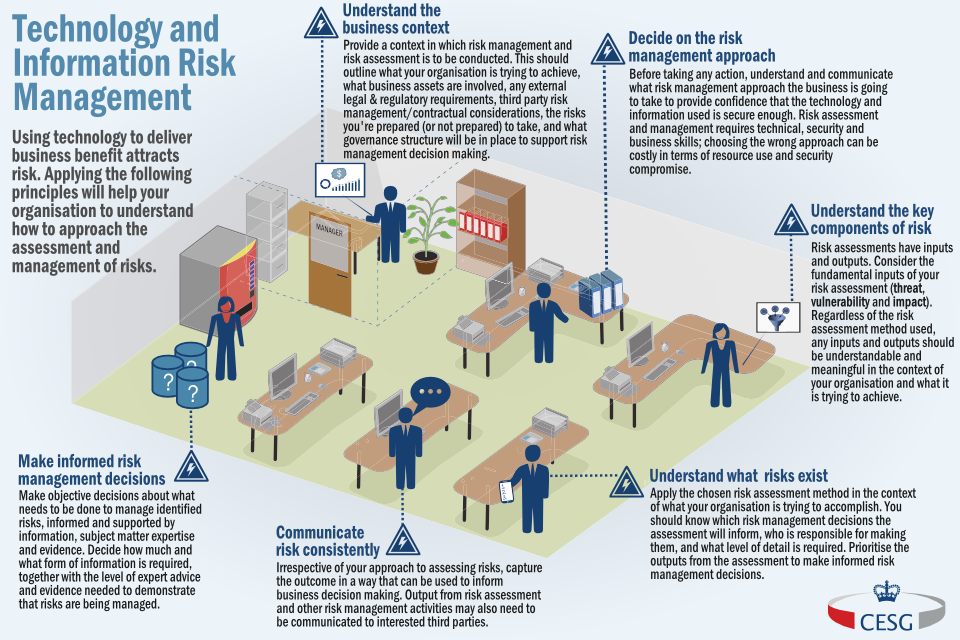
Managing Information Risk - Detailed Guidance - GOV.UK
 www.gov.uk
www.gov.uk
risk management information technology managing system gov guidance infographic service glance assets office data here digital
10+ Security Risk Assessment Templates - Free Samples, Examples
 www.template.net
www.template.net
risk security assessment template information examples templates samples kpmg assets
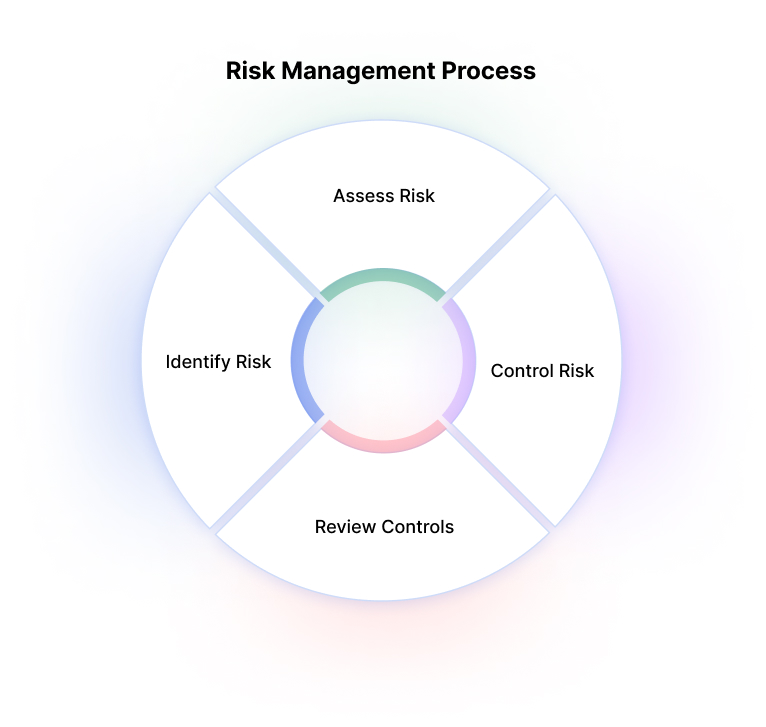
Risk Management Process
 www.imperva.com
www.imperva.com
Risks | Free Full-Text | Context-Based And Adaptive Cybersecurity Risk
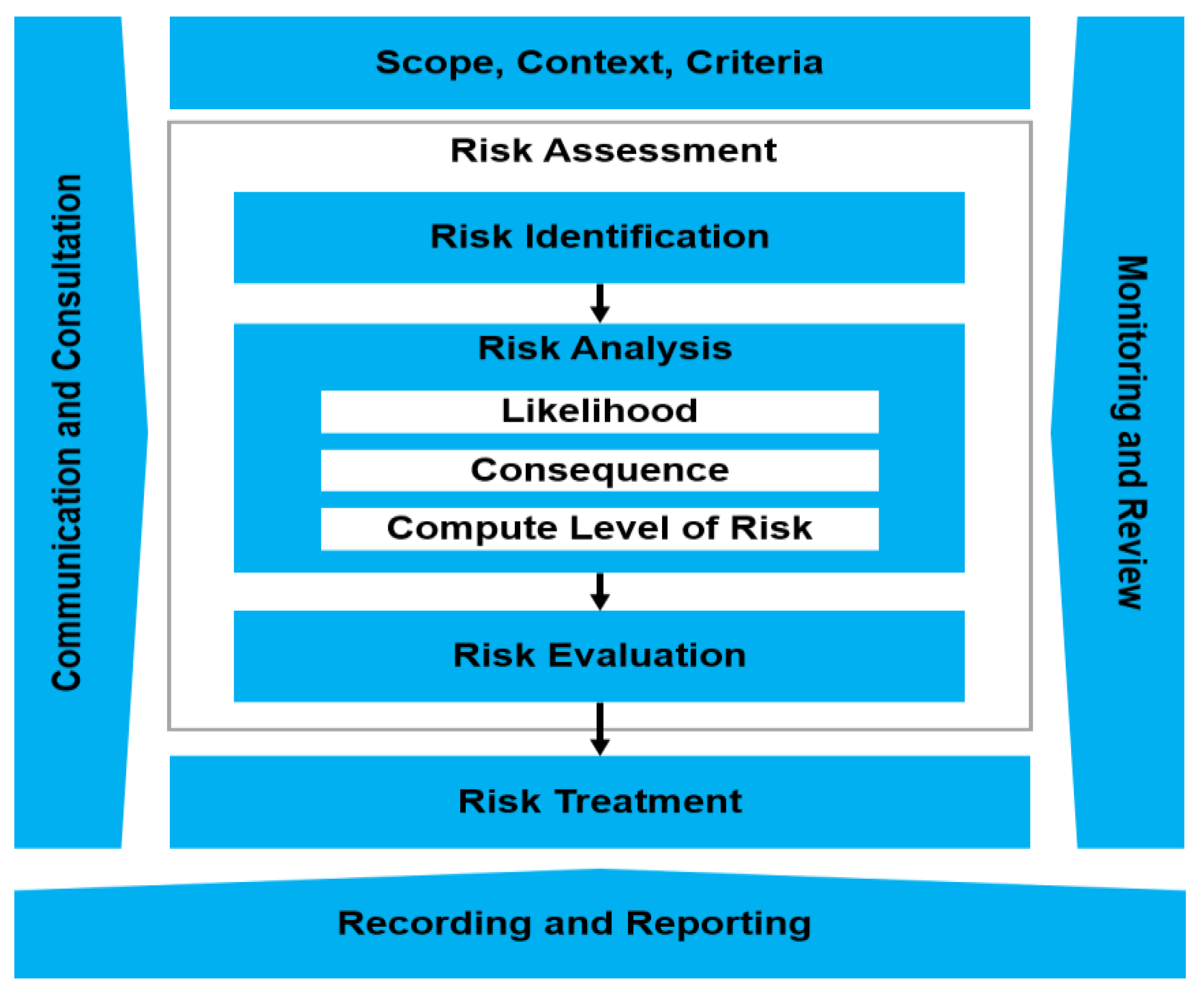 www.mdpi.com
www.mdpi.com
Information Security Risk Management: Build A Strong Program
 phoenixnap.com
phoenixnap.com
Information Security Risk Management | 360factors
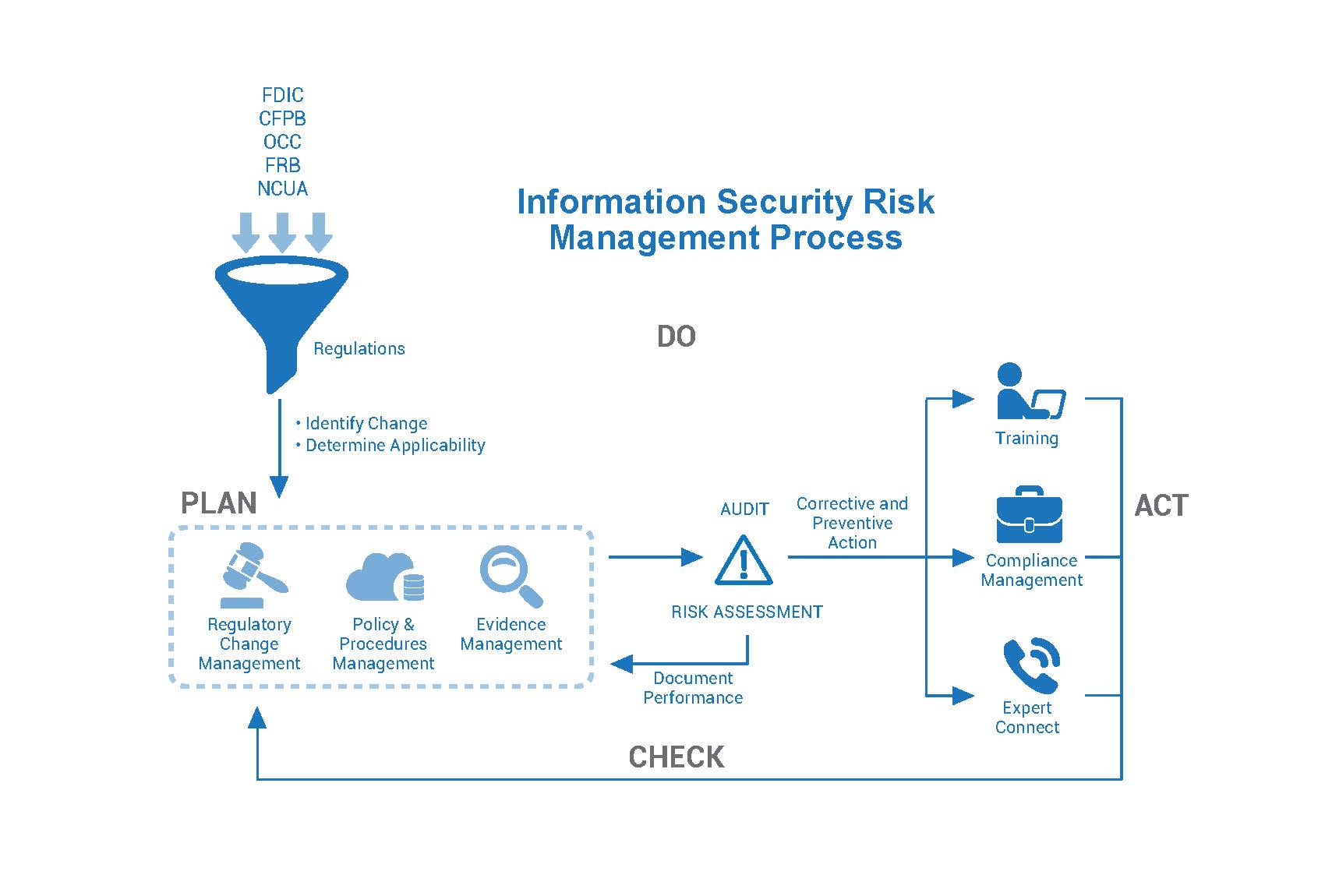 www.360factors.com
www.360factors.com
process management compliance aml risk safety system security bsa quality nerc orsa sox operational complaint diagram environmental information anti hipaa
Creating A Risk Register For Information Security Risk And Compliance
 www.standardfusion.com
www.standardfusion.com
creating update maintained
Creating A Risk Register For Information Security Risk And Compliance
 www.standardfusion.com
www.standardfusion.com
risk register security information management process creating identification risks overview business 2021 which
Defining Information Security Risk Sources: Information Security Risk
 financialcrimeacademy.org
financialcrimeacademy.org
Realizing An Information Security Risk Management
 swimlane.com
swimlane.com
risk framework risks swimlane managing infosec realizing interdependent factors delves subtext threats
Research HQ | Risk Management Framework (RMF): An Overview - Research HQ
 www.researchhq.net
www.researchhq.net
risk framework rmf security cybersecurity
Information Security Risk Management Dashboard Ppt Icon Examples
Risk framework risks swimlane managing infosec realizing interdependent factors delves subtext threats. Information system security and risk administration plan roles and. Information security risk management: build a strong program