← summary report salesforce Salesforce tabular reportes yesware berichten formatieren asignar dashboards lex implementation suspicious activity key words Sar suspicious activity report acronym business stock vector (royalty →
If you are searching about PPT - SUSPICIOUS ACTIVITY DETECTION PowerPoint Presentation, free you've visit to the right place. We have 35 Pictures about PPT - SUSPICIOUS ACTIVITY DETECTION PowerPoint Presentation, free like Recognizing the Signs of Suspicious Activity - Talon Premier Security, Homeland Security on Twitter: "When reporting suspicious activity to and also Understanding the Basics of a Suspicious Activity Report (SAR) - SaferWatch. Here it is:
PPT - SUSPICIOUS ACTIVITY DETECTION PowerPoint Presentation, Free
 www.slideserve.com
www.slideserve.com
suspicious activity detection introduction ppt powerpoint presentation
Threat Removal Guide: Get Rid Of Security Error Detected Due To
 threatremovalguide.blogspot.com
threatremovalguide.blogspot.com
detected popup suspicious activity rid
9 Suspicious Activity Examples + How To Identify & Report Them - Blog
 www.unit21.ai
www.unit21.ai
9 Suspicious Activity Examples + How To Identify & Report Them - Blog
 www.unit21.ai
www.unit21.ai
Suspicious Activity Reports, Explained - ICIJ
 www.icij.org
www.icij.org
suspicious fincen sar icij
Monitor Suspicious Activities, Security Agencies Alerted - News
 www.khaleejtimes.com
www.khaleejtimes.com
How To Protect Yourself From Cybersecurity Threats
 blog.bibank.com
blog.bibank.com
music video animated suspicious activity sundstedt leads marketing animation warning production generating network cybersecurity threats protect yourself security
Cyber Security Checklist [Infographic] - SecurityHQ
![Cyber Security Checklist [Infographic] - SecurityHQ](https://www.securityhq.com/wp-content/uploads/2022/08/SecurityHQ-Infographic-Cyber-Security-Checklist-531x1024.png) www.securityhq.com
www.securityhq.com
Suspicious Activity Detection: What Should Be Reported To Security
 www.msasecurity.net
www.msasecurity.net
suspicious
What Are Suspicious Activity Reports (SARs)? | Persona
 withpersona.com
withpersona.com
Security Awareness: Identifying And Reporting Suspicious Activity | TDECU
 www.tdecu.org
www.tdecu.org
How To Identify Suspicious Activity, Phishing Scams, And Potential
 solutlinko.blogspot.com
solutlinko.blogspot.com
Sources For Identifying Suspicious Activity
 financialcrimeacademy.org
financialcrimeacademy.org
Suspicious Activity Reporting: Indicators And Examples - Fill Out, Sign
 www.templateroller.com
www.templateroller.com
activity suspicious pdf indicators reporting examples online templateroller fill
Recognizing The Signs Of Suspicious Activity - Talon Premier Security
How To Ensure Effective Suspicious Activity Reporting?
 amluae.com
amluae.com
Tips For Safeguarding Against Cyberthreats - Wells Fargo Stories Tips
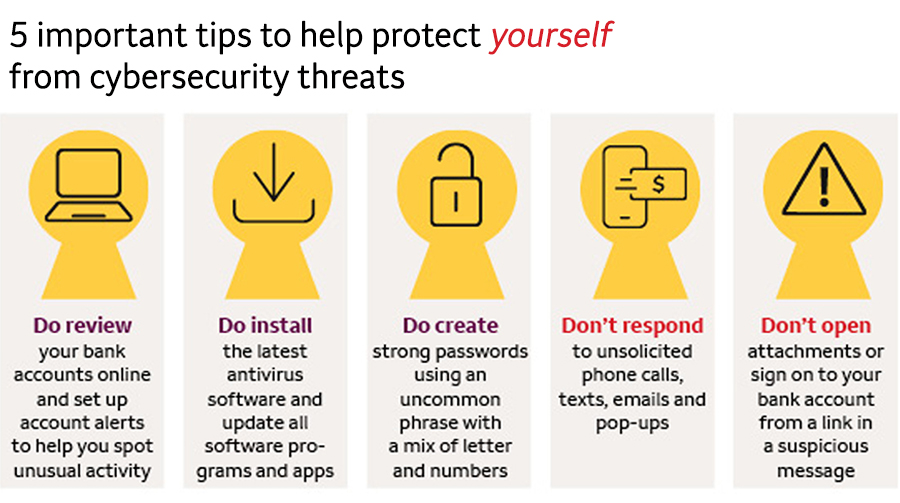 stories.wf.com
stories.wf.com
tips cybersecurity against protect threats yourself safeguarding cyberthreats stories awareness account using
In The Security Control Room Officer Monitors Multiple Screens For
 www.alamy.com
www.alamy.com
Homeland Security On Twitter: "When Reporting Suspicious Activity To
 twitter.com
twitter.com
Nationwide Suspicious Activity Reporting (SAR) Initiative (NSI
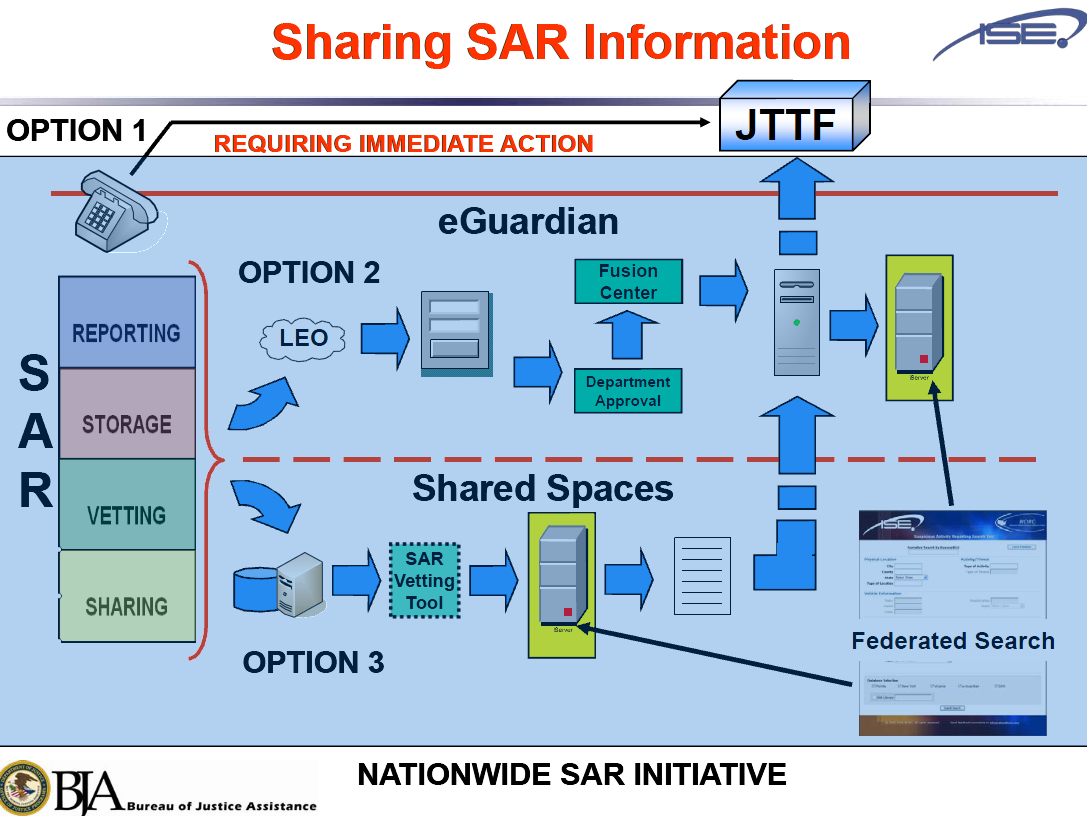 publicintelligence.net
publicintelligence.net
suspicious activity reporting nsi nationwide initiative sar department police seattle phoenix arizona washington publicintelligence
Detecting Suspicious Activities In The Network | The StationX Cyber
Infographic: What Suspicious Activity To Look For To Spot A Thief
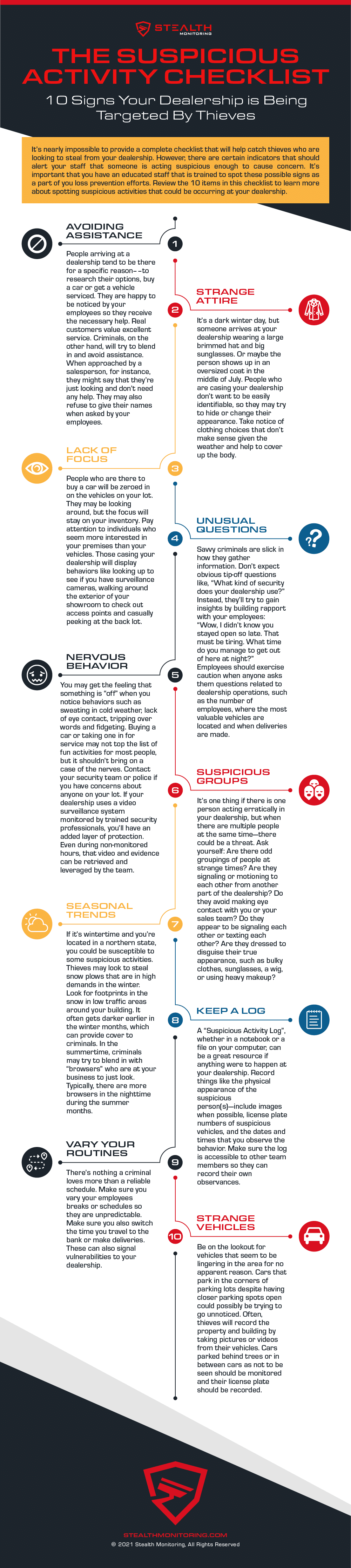 stealthmonitoring.com
stealthmonitoring.com
How To Tell If Someone Is Suspicious - The Security Guards Way - SSC
 www.sscsecurityguardtraining.com
www.sscsecurityguardtraining.com
WHAT IS SUSPICIOUS ACTIVITY?
 www.linkedin.com
www.linkedin.com
CSAM Week 3: Recognizing, Reporting Phishing > Defense Contract
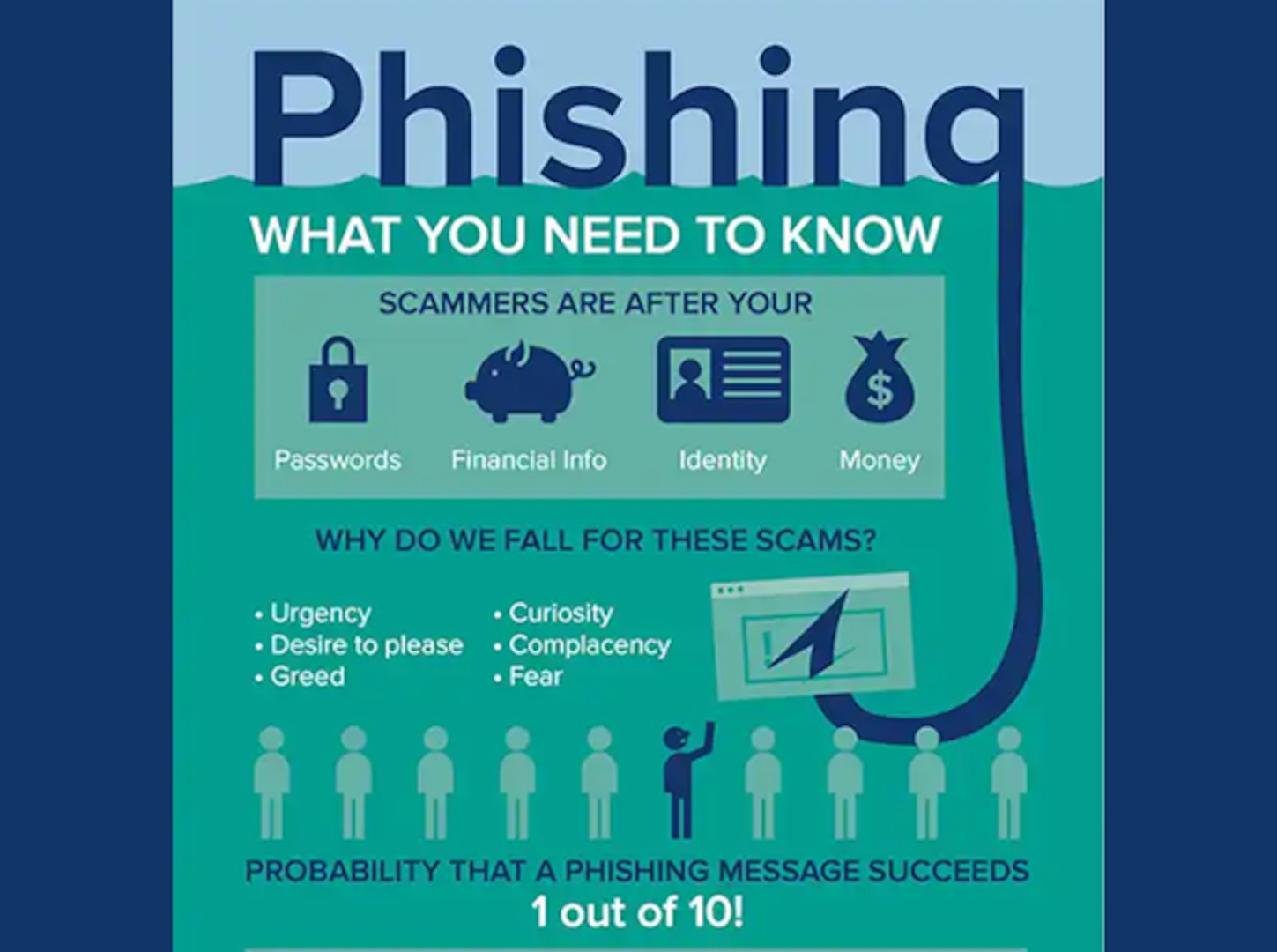 www.dcma.mil
www.dcma.mil
How To Detect New Threats Via Suspicious Activities - Sigma Cyber Security
 sigmacybersecurity.com
sigmacybersecurity.com
Understanding The Basics Of A Suspicious Activity Report (SAR) - SaferWatch
 www.saferwatchapp.com
www.saferwatchapp.com
In The Security Control Room Two Officers Monitoring Multiple Screens
 www.alamy.com
www.alamy.com
Suspicious Activity Alerts - Centennial Bank
 www.my100bank.com
www.my100bank.com
activity alerts suspicious banking personal
In The Security Control Room Officer Monitors Multiple Screens For
 www.alamy.com
www.alamy.com
Security Guard Speaking Microphone When Noticing Stock Photo 2265036249
 www.shutterstock.com
www.shutterstock.com
In The Security Control Room Officer Monitors Multiple Screens For
 www.alamy.com
www.alamy.com
How To Report Suspicious Activity In Your Neighborhood - SaferWatch
 www.saferwatchapp.com
www.saferwatchapp.com
Suspicious Activity | MemberGate Membership Site Software
 www.membergate.com
www.membergate.com
suspicious activity proactive measures security different place has
Understanding The Basics Of A Suspicious Activity Report (SAR) - SaferWatch
 www.saferwatchapp.com
www.saferwatchapp.com
Cyber security checklist [infographic]. In the security control room two officers monitoring multiple screens. Sources for identifying suspicious activity